MRX20 Mission to Mars Mission 1: Secure Transmission Feed Mission 2: ICSA Files Mission 3: Steganography Mission 4: Visual Cryptography
MRX20 Mission
The MRX20 probe was sent to Mars by the Inter-Continental Space Agency (ICSA) a few years ago. It was due to return to planet Earth just a few days ago. The probe collected a large amount of samples from the Martian soil and took thousands of high definition pictures of Mars. Initial analysis performed on site by the probe's Artificial Intelligence seems to indicate that the probe may contain strong evidence that there is life on Mars.
Unfortunately just a few thousand miles away from Earth, the probe collided with an unidentified geostationary satellite. It was pulverised into small pieces. Most of these were either lost in space or burnt down when entering the Earth's atmosphere. A few pieces did pierce through the atmosphere and crashed on Earth in various locations all around the globe.
The ICSA sent a team of Probe Debris Collectors (PDCs) to locate the various parts and submit back to the ICSA the exact locations and pictures of the debris found. Each PDC has been instructed to communicate with the ICSA using a secure connection using a range of encoding/encryption techniques.
The What3Words (W3W) geo-localisation system is used to inform of the exact location of the debris. Your mission is to decode the secured transmission messages to locate the position of the debris and to retrieve all the information that has been retrieved from the debris. Use this information to find out what you can learn about the existence of life on planet Mars.
Mission 1: Secure Transmission Feed
Message #1 - received at 7:46am - Encryption: Pigpen Cipher

Message #2 - received at 8:54am - Encryption: Pigpen Cipher
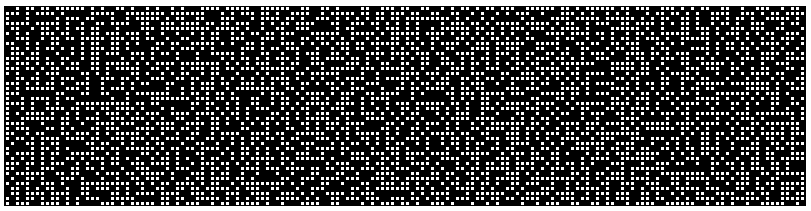
Message #3 - received at 9:08pm - Encoding: Morse Code

Message #4 - received at 10:51am - Encoding: Morse Code

Message #5 - received at 11:42pm - Encoding: Nautical Signal Flags
Message #6 - received at 12:16pm - Encoding: Nautical Signal Flags
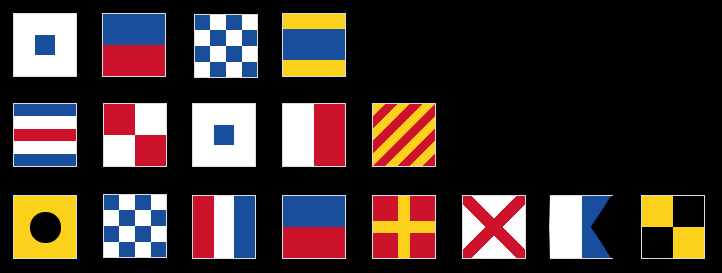
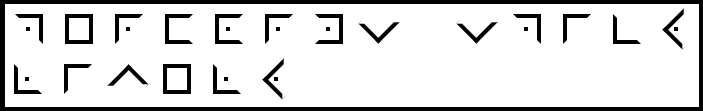
Message #7 - received at 16:17pm - Encoding: Semaphore
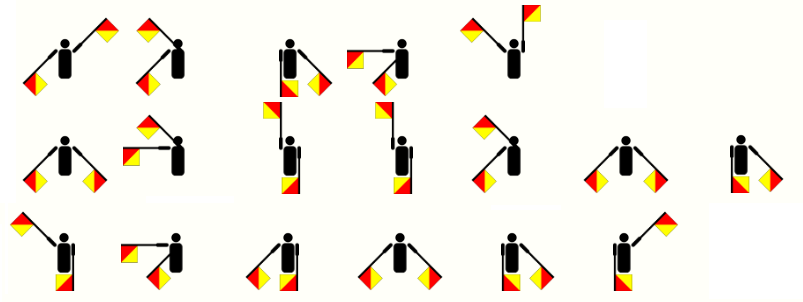
Message #8 - received at 19:28pm - Encoding: Semaphore
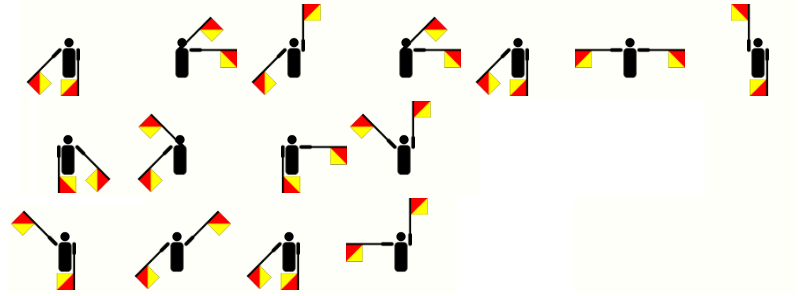
Message #9 - received at 20:25pm - Encryption: Railfence Cipher

Message #10 - received at 21:34pm - Encryption: Railfence Cipher

Message #11 - received at 22:02pm - Encryption: Caesar Shift

Message #12 - received at 23:56pm - Encryption: Caesar Shift
World Flags
| Flag A | Flag B | Flag C | Flag D | Flag E | Flag F |
 |  |  |  |  | 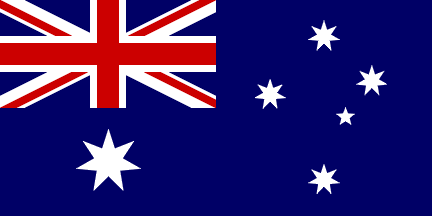 |
| Flag G | Flag H | Flag I | Flag J | Flag K | Flag L |
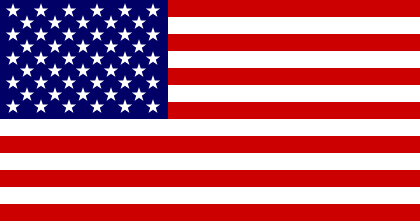 | 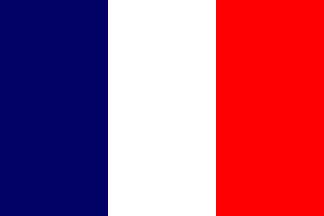 |  | 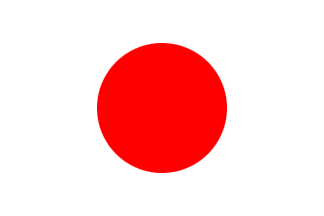 | 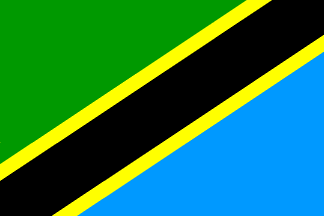 |  |
W3W Geo-Localisation
After decoding all 12 messages, input the three words from each of the received messages in the table below. Use the what3words.com geo-localisation website to identify the exact location and country of where the debris where found. Find the corresponding flag using the 12 flags listed below and input the letter attached to each flag in the drop down list corresponding to each message.Message #1 - W3W: // - Flag:
Message #2 - W3W: // - Flag:
Message #3 - W3W: // - Flag:
Message #4 - W3W: // - Flag:
Message #5 - W3W: // - Flag:
Message #6 - W3W: // - Flag:
Message #7 - W3W: // - Flag:
Message #8 - W3W: // - Flag:
Message #9 - W3W: // - Flag:
Message #10 - W3W: // - Flag:
Message #11 - W3W: // - Flag:
Message #12 - W3W: // - Flag:
Mission Code
Mission 2: ICSA Secure File System
All ICSA files are encrypted using a mono-alphabetic substitution cipher. A mono-alphabetic cipher (aka simple substitution cipher) is a substitution cipher where each letter of the plain text is replaced with another letter of the alphabet. It uses a fixed key which consist of the 26 letters of a “shuffled alphabet”. You will need to use a frequency analysis to decrypt these files.
BNXC QC TSR HUVXTS LPNZRT HXUB TSR CVZ NZK TSR CRJUZK-CBNPPRCT LPNZRT QZ TSR CUPNX CMCTRB NHTRX BRXJVXM. QZ RZDPQCS, BNXC JNXXQRC N ZNBR UH TSR XUBNZ DUK UH FNX NZK QC UHTRZ XRHRXXRK TU NC TSR 'XRK LPNZRT'. TSR PNTTRX XRHRXC TU TSR RHHRJT UH TSR QXUZ UOQKR LXRGNPRZT UZ BNXC' CVXHNJR, FSQJS DQGRC QT N XRKKQCS NLLRNXNZJR KQCTQZJTQGR NBUZD TSR NCTXUZUBQJNP AUKQRC GQCQAPR TU TSR ZNYRK RMR.
BNXC QC N TRXXRCTXQNP LPNZRT FQTS N TSQZ NTBUCLSRXR, SNGQZD CVXHNJR HRNTVXRC XRBQZQCJRZT AUTS UH TSR QBLNJT JXNTRXC UH TSR BUUZ NZK TSR GNPPRMC, KRCRXTC, NZK LUPNX QJR JNLC UH RNXTS.
TSR KNMC NZK CRNCUZC NXR PQYRFQCR JUBLNXNAPR TU TSUCR UH RNXTS, ARJNVCR TSR XUTNTQUZNP LRXQUK NC FRPP NC TSR TQPT UH TSR XUTNTQUZNP NOQC XRPNTQGR TU TSR RJPQLTQJ LPNZR NXR GRXM CQBQPNX.
BNXC QC TSR CQTR UH UPMBLVC BUZC, TSR PNXDRCT GUPJNZU NZK SQDSRCT YZUFZ BUVZTNQZ UZ NZM LPNZRT QZ TSR CUPNX CMCTRB, NZK UH GNPPRC BNXQZRXQC, UZR UH TSR PNXDRCT JNZMUZC QZ TSR CUPNX CMCTRB. TSR CBUUTS AUXRNPQC ANCQZ QZ TSR ZUXTSRXZ SRBQCLSRXR JUGRXC 40% UH TSR LPNZRT NZK BNM AR N DQNZT QBLNJT HRNTVXR. BNXC SNC TFU BUUZC, LSUAUC NZK KRQBUC, FSQJS NXR CBNPP NZK QXXRDVPNXPM CSNLRK.
YHT CYWQUZHTOT QV WCOU NU YHT SCGTO QV JCU UXOOQXPLNPJ WCOU. NY NU ZONWCONSG MQWZQUTL QV MCORQP LNQKNLT (95.32%), WQSTMXSCO PNYOQJTP (2.6%) CPL COJQP (1.9%). NY CSUQ MQPYCNPU YOCMT STITSU QV DCYTO ICZQO, QKGJTP, MCORQP WQPQKNLT, HGLOQJTP CPL QYHTO PQRST JCUTU. YHT CYWQUZHTOT QV WCOU NU WXMH YHNPPTO YHCP TCOYH'U. YHT UXOVCMT ZOTUUXOT NU QPSG CRQXY 610 ZCUMCSU DHNMH NU STUU YHCP 1% QV YHT TCOYH'U ICSXT. YHT MXOOTPYSG YHNP WCOYNCP CYWQUZHTOT ZOQHNRNYU YHT TKNUYTPMT QV SNBXNL DCYTO CY YHT UXOVCMT QV WCOU, RXY WCPG UYXLNTU UXJJTUY YHCY YHT WCOYNCP CYWQUZHTOT DCU WXMH YHNMFTO NP YHT ZCUY. YHT HNJHTUY CYWQUZHTONM LTPUNYG QP WCOU NU TBXCS YQ YHT LTPUNYG VQXPL 35 FW CRQIT YHT TCOYH'U UXOVCMT. YHT CYWQUZHTOT QV WCOU HCU RTTP SQUNPJ WCUU YQ UZCMT YHOQXJHQXY HNUYQOG, CPL YHT STCFCJT QV JCUTU UYNSS MQPYNPXTU YQLCG.
YHT CYWQUZHTOT QV WCOU NU MQSLTO YHCP TCOYH'U. QDNPJ YQ YHT SCOJTO LNUYCPMT VOQW UXP, WCOU OTMTNITU STUU UQSCO TPTOJG CPL HCU C SQDTO TVVTMYNIT YTWZTOCYXOT (CRQXY 210 F). YHT CITOCJT UXOVCMT TWNUUNQP YTWZTOCYXOT QV WCOU NU EXUY 215 F, DHNMH NU MQWZCOCRST YQ NPSCPL CPYCOMYNMC. YHT DTCFTO JOTTPHQXUT TVVTMY NP YHT WCOYNCP CYWQUZHTOT (5 °M, ITOUXU 33 °M QP TCOYH) MCP RT TKZSCNPTL RG YHT SQD CRXPLCPMT QV QYHTO JOTTPHQXUT JCUTU. YHT LCNSG OCPJT QV YTWZTOCYXOT NP YHT SQDTO CYWQUZHTOT NU HXJT (MCP TKMTTL 100 °M PTCO YHT UXOVCMT NP UQWT OTJNQP) LXT YQ YHT SQD YHTOWCS NPTOYNC. YHT YTWZTOCYXOT QV YHT XZZTO ZCOY QV YHT WCOYNCP CYWQUZHTOT NU CSUQ UNJPNVNMCPYSG SQDTO YHCP TCOYH'U RTMCXUT QV YHT CRUTPMT QV UYOCYQUZHTONM QAQPT CPL YHT OCLNCYNIT MQQSNPJ TVVTMY QV MCORQP LNQKNLT CY HNJHTO CSYNYXLTU.
LXUY LTINSU CPL LXUY UYQOWU COT ZOTICSTPY QP WCOU, DHNMH COT UQWTYNWTU QRUTOICRST RG YTSTUMQZTU VOQW TCOYH. ZSCPTY-TPMNOMSNPJ LXUY UYQOWU (JSQRCS LXUY UYQOWU) QMMXO QP CITOCJT TITOG 5.5 TCOYH GTCOU QP WCOU CPL MCP YHOTCYTP YHT QZTOCYNQP QV WCOU OQITOU. HQDTITO, YHT WTMHCPNUW OTUZQPUNRST VQO YHT LTITSQZWTPY QV SCOJT LXUY UYQOWU NU UYNSS PQY DTSS XPLTOUYQQL.
YHT WCOYNCP CYWQUZHTOT NU CP QKNLNANPJ CYWQUZHTOT. YHT ZHQYQMHTWNMCS OTCMYNQPU NP YHT CYWQUZHTOT YTPL YQ QKNLNAT YHT QOJCPNM UZTMNTU CPL YXOP YHTW NPYQ MCORQP LNQKNLT QO MCORQP WQPQKNLT. CSYHQXJH YHT WQUY UTPUNYNIT WTYHCPT ZOQRT QP YHT OTMTPYSG SCXPMHTL TKQWCOU YOCMT JCU QORNYTO VCNSTL YQ VNPL WTYHCPT NP YHT CYWQUZHTOT QITO YHT DHQST WCOU, UTITOCS ZOTINQXU WNUUNQPU CPL JOQXPL-RCUTL YTSTUMQZT LTYTMYTL XPTKZTMYTL STITSU QV WTYHCPT NP YHT WCOYNCP CYWQUZHTOT, DHNMH WCG TITP RT C RNQUNJPCYXOT VQO SNVT QP WCOU.
In order to decode the content of this file, you will need to program your own Caesar Cipher Decoder.
You will then be able to use your decoder to decrypt each line of this file one, line at a time.
Encrypted File Content:
Line 1:
OPNO JVUJLUAYHAPVU VM TLAOHUL NHZ OHZ ILLU TLHZBYLK PU AOL HSNH JYHALY.
Line 2:
DAIMAV OSLWJ OSK XGMFV DWKK LZSF KAP EWLWJK TWDGO LZW KMJXSUW.
Line 3:
KPGXDJH BXCTGPA STEDHXIH LTGT UDJCS LWTC PCPANHXCV IWT HDXA XC IWT PGTP.
Line 4:
CYWO YBQKXSM NOZYCSDC GOBO PYEXN GRSMR COOWC DY MYXPSBW DRO ZBOCOXMO YP K PYBW YP VSPO YX ZVKXOD WKBC.
Mission 3: Steganography


The following pictures were retrieved from the probe's hard drive. There is a chance that they contain hidden information that could confirm the existence of life on Mars.
The technique used to hide information within a picture is called steganography. A range of online tools enable you to hide or reveal information on/from a picture.
The following websites may help you find out if these pictures contain hiden information:
Visual Cryptography
Visual cryptography is a technique used to reveal a secret message when overlapping two semi-transparent pictures. The following 2 pictures where retrieved from the probe's ROM and may contain the probe's unique identifier. Will you be able to reveal this unique ID:Picture 1:
Picture 2: