Code Breaking during WWII

The Enigma machines are a series of electro-mechanical rotor cipher machines. The first machines were invented at the end of World War I by German engineer Arthur Scherbius and were mainly used to protect commercial, diplomatic and military communication. Enigma machines became more and more complex and were heavily used by the German army during World War II to encrypt radio signals.
One of the key objectives for the Allies during WWII was to find a way to break the code to be able to decrypt German communications. A team of Polish cryptanalysts was the first to break Enigma codes as early as 1932, however the German used more advanced Enigma machines making it virtually impossible to break the Enigma code using traditional methods. In 1939, with the prospect of war, the Poles decided to share their findings with the British. Dilly Knox, one of the former British World War I Codebreakers, set up an Enigma Research Section at Bletchley Park, England. He worked alongside Tony Kendrick, Peter Twinn, Alan Turing and Gordon Welchman. Together they developed a complex machine called the Bombe used to workout Enigma settings from intercepted German communications. The first wartime Enigma messages were broken in January 1940. Being able to decrypt German messages gave the Allies valuable information which has had a major impact on the outcomes of WWII.
To gain a better understanding of the encryption techniques used by the Enigma machine we have decided to recreate a virtual Enigma machine/emulator.
You you will be able to use this machine to both encrypt or decrypt Enigma messages (Enigma encryption is symmetric, which means that the same settings can be used to both encrypt or decrypt a message).
Enigma Machine Emulator
Please note that this emulator is a Beta version.
To use this Enigma machine:
- Check the code book which is provided (see links on the left hand side) to select the desired settings. Germans used to change the Enigma settings at least once a day. They used code books that listed all the settings to use for every day of the month. This information is essential to both encrypt and decrypt messages.
- Click on the three rotors (upper section of the Enigma machine) to configure the rotor settings.
- Click on the various plugs on the plugboard (lower section of the Enigma machine) to configure/wire the plugboard.
- Type your message using the keyboard of the machine (3rd section of the machine, just above the plugboard).
- Each letter will be encrypted as it is typed. The lamp of the corresponding encrypted letter will turn on on the lampboard section of the machine (2nd section, below the rotors).
- Our emulator will also note down both the message you typed and the encrypted message in the note book appearing just below the Enigma machine.
Inside the Enigma
The enigma machine is a fairly complex encryption machine which consists of four main sections: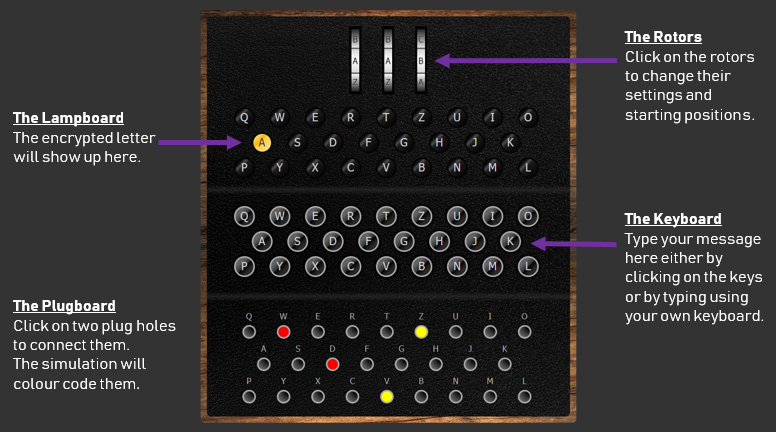
The Keyboard
The keyboard is used to retrieve the user input. The Enigma machine is a symmetric encryption machine. Which means that it can be used to both encrypt or decrypt a message using the same settings. The keyboard is hence used to either enter the plaintext that needs to be encrypted or the ciphertext that needs to be decrypted.
They keyboard consists of 26 keys for each letter of the alphabet. This means that encrypted messages will be joined up without any spaces or punctuation signs.
Notice how the keyboard starts with the letters QWERTZ instead of QWERTY. This is due to the fact that in the German language, the letter Z is more often used than the letter.
The plugboard
Once a key is pressed on the keyboard, it goes through the plugboard which provides the first stage of the encryption process. It is based on the principles of a substitution cipher, a form of transposition encryption.
To setup the keyboards, short wires are used to connect pairs of letters that will be permuted. For instance on the picture below the letter W will be replaced with a D and the letter D with a W as a (red) wire is used to connect these two letters/plugs. Similarly, letter V will become letter Z and Z will become V.

In a code book the plugboard settings would be recorded as follows: DW VZ
The Rotors
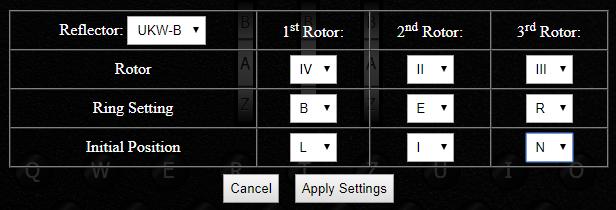
After the plugboard, the letter goes through the three rotors in order (from right to left), each of them changing it differently using a combination of transposition cipher and Caesar cipher! On the engima M3 there are three rotor slots and five rotors to choose from. Each rotor is identified using a Roman numeral from I to V. This provides a few settings of the Enigma machine: which rotors to use, and in which order to position them. In a code book this seeting would be recorded as IV II III (Left, Middle and Right rotors).
Each of the five rotors encrypt the letter differently using a transposition/permutation cipher and can be connected in the Enigma machine with a different Ring setting. Another setting is the initial position of the rotors: Which letters are you going to set each rotor to begin with (e.g. A/B/C../Z sometimes recorded in a codebook using numbers (01 for A, 02 for B up to 26 for Z). This creates a Caesar Shift (Caesar Cipher). On an Enigma machine, you can change the position of the rotors by turning the three wheels.
Different versions of Enigma (e.g. M4) included four rotors which made the encryption process and the number of possible settings even bigger.
On our Enigma M3 emulator, you can click on the rotors to access the Enigma rotors settings:

What makes the Enigma code particularly difficult to crack is that every time a key is pressed, the rotor on the right turns by 1 letter. Which means that the encryption settings constantly changes for each letter of a message. It also means that a single plaintext letter would be encrypted differently depending on its position in the message.
The rotors are also connected to each other so that when the rotor positioned on the right reach a specific letter, it triggers the rotor in the middle to rotate by one letter. Similarly when the rotor in the middle reaches a specific letter it triggers the rotor on the left to turn by one letter.
You will find more information on how the rotors operate on the following wikipedia page.
The Reflector
The reflector is another type of rotor inside the machine. Once the letter has gone through the three rotors from right to left, the reflector will reflect the electrical current back through the rotors, sending the encrypted letter through the rotors from left to right for another 3 stages of encryption and then through the plugboard again for a final substitution cipher. When going through the reflector, a permutation cipher is also applied to the letter.
Different versions of reflectors were used on different versions of Enigma machines. Each reflector would apply a different permutation cipher. Enigma M3 machines were equipped with either a UKW-B or UKW-C reflector. You can apply these two reflectors in the rotor settings window of our emulator (see screenshot above).
The diagram below shows the journey of a letter through the encryption process of an Enigma M3.
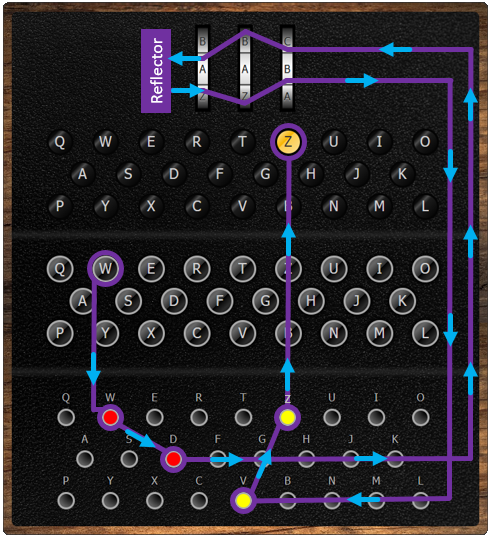
The lampboard
The lampboard is the final stage of the encryption process and is used to show the output (encrypted letter). It consists of 26 light bulbs, one for each letter of the alphabet.German Translation Book
Code breakers working at Bletchley Park had to decrypt German communications. Some understanding of the German language was needed to be able to understand the decrypted messages. Here are a few words or expressions that were often used in German communications.
U-Boot: U-Boat
Keine besonderen Ereignisse: Nothing to report
Warten auf Anweisungen: Waiting for instructions
Numbers from 1 to 10: Eins, Zwei, Drei, Vier, Fünf, Sechs, Sieben, Acht, Neun, Zehn.
Days of the week (Monday to Sunday): Montag - Dienstag - Mittwoch - Donnerstag - Freitag - Samstag - Sonntag
Wir sind: We are / Wir werden: We will / Wir haben: We have
Angreifen: To Attack
Ziel: Target / Ziel zerstört: Target Destroyed
Hafen: Port
Nächsten: Next / Von: Of
Wettervorhersage: Weather forecast
Mission X
Dear code breaker,
I am contacting you from Bletchley Park as we are intercepting an increased volume of encrypted radio signals. We are working day and night to break the Enigma codes that the German Navy are updating every day. The German U-Boats are operating in the Atlantic Ocean and are causing major casualties by sinking not only military ships from the Royal Navy but also merchant ships bringing supplies from the United States and Canada to the United Kingdom.
Luckily, we have gained access to a code book which, we believe gives us all the settings for the Enigma M3 machine, for each day of this month.
Could you help us decode the following secret messages by applying the required settings to the Enigma M3 machine. I am not sure about your understanding of the German language so I have enclosed a German translation book including key German expressions.
We believe that the Germans are preparing a major attack on the south coast of England. We hope that the messages will help us find more information on the exact location and day of the attack.
Let us know if you can find out more useful information from these messages.
Yours sincerely,
Your friend, Alan T.
Message #1 - Received on 7 April 1940
Message #2 - Received on 11 April 1940
Message #3 - Received on 12 April 1940
Message #4 - Received on 12 April 1940
Bletchley Park

The Bletchley Park code breaking organisation started in 1939 with only around 150 staff. This number grew significantly during the war up to around 9000 people working for the organisation. Some of the famous code breakers who worked at Bletchley Park include Dilly Knox, Nigel de Grey, Alan Turing, Gordon Welchman and Bill Tutte.
People working at Bletchley Park had to sign the official secrecy act, promising that they wouldn’t tell anybody, even their closest friends or family, where they were working and what they were doing. This meant that staff had to create their own cover stories for their job. Also, no-one was allowed to bring files about the work done at Bletchley Park or, in fact, anything that might help the enemy outside of the park. German spies could have been anywhere during World War II, so it was important for Bletchley Park code breakers to remain secretive about their work.
The codebreaking operations at Bletchley Park came to an end in 1946 and all information about the wartime operations remained classified for a few decades. A lot of information and equipment was destroyed after the war. The contribution of code breakers from Bletchley Park during the war was only revealed to the public in the mid 70s. After this time, staff at Bletchley Park were finally allowed to say where they had worked.

If Alan Turing and his team had not broken the Enigma code, historians estimate that the war would have gone on for at least another two years. Alan Turing saved a further 14-21 million lives with his machine, but the general public knew nothing about him until after he died.
For more information about Bletchley Park, the Enigma and the work of code breakers during World War II, visit the Bletchley Park website. A working reconstruction of the Turing-Welchman Bombe, the machine designed at Bletchley Park to break the Enigma code, is also on display at The National Museum of Computing (alongside other wartime machines used during World War II such as Colossus the world's first electronic computer which was also used to decipher Lorrentz-encrypted messages).
Enigma M3 


Our Enigma machine emulator is replicating the encryption process of the Enigma M3 series that was used by the German Navy (Kriegsmarine). It is fitted with a UKW-B reflector. Later on through the war, it was replaced by the M4 series which included a 4throtor.
Before pressing any keys on the keyboard section of the machine you will need to apply the required settings. To do so you will need to click on the rotors to adjust the wheels initial settings and then make the required connections by clicking on the different plugs (bottom section of the machine) to connect letters from the plugboard. Actual Enigma settings are defined in the code book provided (see link on the left).
| Reflector: | 1st Rotor: | 2nd Rotor: | 3rd Rotor: |
| Rotor | |||
| Ring Setting | |||
| Initial Position |
Enigma Code Book
Code books were used by the Germans to list all the settings needed to set up the Enigma machines before starting to encrypt or decrypt messages. The Germans used to change the Enigma settings very regularly (e.g. once a day) so that if the Allies managed to break their code (find out the Enigma settings) they would only be able to use them for that day and would have to find the new settings every day. Code books were highly confidential documents as if a codebook was captured or reconstructed, messages could easily be decrypted.
An Enigma code book would have one page per month. The page would include all the settings for each day of the month with the first day of the month at the bottom of the page so that once used, a setting could be torn off the page.
The settings would indicate which rotors to use and in which order to connect them. Initially the Enigma machine came with a box of five rotors to choose from. On an Enigma M3, three out of the five rotors were connected. The M4 Enigma used four rotors chosen from a box of up to eight rotors.
The settings would also include the wheel settings (how to connect the rotors) and their initial position. Finally the settings would indicate which letters to connect by plugging cables on the plugboard.
Enigma M3 Code Book (UKW-B Reflector) - April 1940
| Datum [Date] |
Walzenlage [Rotors] |
Ringstellung [Ring settings] |
Steckerverbindungen [Plugboard settings] |
Grundstellung [Initial rotor positions] |
|---|---|---|---|---|
| 30 | AKK | FDV | ||
| 29 | JHS | OTO | ||
| 28 | DIL | JJK | ||
| 27 | ICC | RXV | ||
| 26 | ECW | GUB | ||
| 25 | MFO | ZBY | ||
| 24 | UCO | BDT | ||
| 23 | RWQ | IYM | ||
| 22 | TRK | SFX | ||
| 21 | CTZ | TQO | ||
| 20 | XOM | DKV | ||
| 19 | LDQ | IAH | ||
| 18 | NWL | HSP | ||
| 17 | HFZ | GPZ | ||
| 16 | UBJ | PJU | ||
| 15 | BCG | KFQ | ||
| 14 | EAP | CCH | ||
| 13 | AOK | DMF | ||
| 12 | CKU | VQN | ||
| 11 | BHN | XIO | ||
| 10 | QKP | MSW | ||
| 9 | UTC | EQL | ||
| 8 | GDJ | PLE | ||
| 7 | WNM | RAO | ||
| 6 | ETT | HXA | ||
| 5 | MHY | XXJ | ||
| 4 | WXE | OFP | ||
| 3 | LIQ | KTR | ||
| 2 | NQC | ZJR | ||
| 1 | IHQ | UJJ |
